
Welcome to Invicta Digital
Old Fashioned Service for New TechnologyInstallation, servicing & repairs for desktops, laptops, tablets, smartphones and many other gadgets One to one, home based training from the absolute beginner to the more experienced.
Cleaning Virus or Malware infection and data recovery a speciality

About Invicta Digital
A Message From SimonOver many years of helping people in the local area, I have learnt that often people both young and old struggle with computers or even refuse to use technology thinking they will be unable to cope. Everyone can operate a computer and access the almost infinite world of the internet with a little help from me.
I am based in the Deal area and offer a cost effective service delivered without the techno-jargon.
So if you need help with your technology problems give me a call today.
Products and Services
Don't you hate it when unexpected bills turn up? That's why I charge a flat £40 per hour (plus any parts needed), with no callout charge for local customers.Protect your information from theft or accidental loss

One area of the internet that often frightens people is the thought that some bad person somewhere in the world will take your personal information and steal your money or worse. Another area less often thought about is one of what happens to all the stuff you have on your computer if it breaks or is stolen. I specialise in computer security and can help you protect your family and your computer by checking that you have a good understanding of internet security and that your information is correctly protected.
Help getting you connected

If you are new to the internet you will probably require an internet connection. I can help you select the best internet company for your needs, set up your new internet connection, make sure the wireless is working correctly, set up internet access where it's required, etc.
Help! My Computer doesn't work or my information has gone

Computers do break, it's a fact of life. Most of the time when a computer fails it's easier and cheaper to buy a new computer. Where I can help is in the transfer of your information from your old broken computer onto your new one. I also have the ability to potentially recover information that has gone missing either through accident or because of a hard drive failure.
Training: From the absolute beginner to the advanced user

If you need assistance in how to use your computer, I can help with friendly, non technical instruction. Whether you are a complete beginner and are trying to send your very first e-mail or you are trying to advance your technology skills and abilities such as designing your own web-site, I can guide you every step of the way.
Is your Computer Getting Old or Slow?

I tell my customers to keep their computer until it doesn't do what they want it to do or it performs unacceptably slow. You would be amazed how much faster your computer would work with a little TLC from me. But in the end your computer will need replacing - I can help with that too.
Web Design

Are you thinking about planting a stake in the world of the internet. I can help write your website in HTML/CSS or WordPress
Help getting you connected
If you are new to the internet you will probably require an internet connection. I can help you select the best internet company for your needs, set up your new internet connection, make sure the wireless is working correctly, set up internet access where it's required, etc.
Useful Web Links
Here's some websites that will give you useful informationI.C.O.
Get Safe Online
Cable.co.uk
Classic Computer Museum
Useful Advice
The Survivor's Guide To The Digital WorldThe Survivor's Guide to Broadband Access
One of the questions I often get asked is “Why is my internet slow and how can I make it faster?”. Well if you ask most broadband providers they will tell you (with a variety of accents) that it’s just because you live where you live. This type of answer is about as useful as “your internet is slow because your broadband box is running out of fairy dust”.
Let me try to explain in layman’s terms the various ways you can access the internet with the pros and cons involved in each method.
Firstly let me say a few words about how the internet speed is measured. I could put on my ceremonial thick lensed spectacles and start talking about how a Megabyte is made up from 8 Megabits and how a Megabit is made up from 1024 Kilobits. But all you need to know is when you send stuff to the internet you are uploading (sometimes called upstream) and when you receive stuff from the internet you are downloading (sometimes called downstream). The upload speed normally is slower than the download speed and you need a download speed of over 3.5 megabits per second (mbps) to watch BBC iPlayer HD videos.
When most people talk about broadband they are describing an ADSL broadband connection. Want to sound like you’re an internet genius? - You do – well the acronym ADSL stands for ‘Asymmetric Digital Subscriber Line’, slip that into your next dinner party and watch the room empty.
The speed of an ADSL connection mainly depends on the length of the bit of copper wire that links your house to your local telephone exchange. Here’s a graph that shows the relationship between internet speed and distance to your exchange. So in simple terms, if you live more than about 3.5 miles away from your local exchange your internet speed will be very slow.
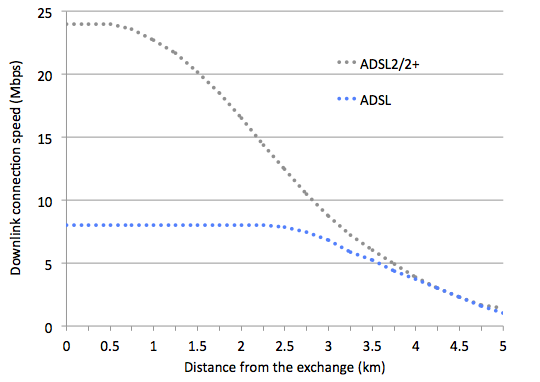
You can somewhat improve a slow ADSL connection by making sure the quality of the copper wire that makes up your telephone cable is as free from interference as possible by removing any internal telephone cables from the equation. That’s why when you phone the helpdesk of your broadband provider they ask you to plug your router into the telephone socket where your BT telephone cable connects to your house.
So what do you do if you live too far away from the exchange for an ADSL broadband connection to work? Well if you’re lucky enough you may have faster internet connections available. The most widely available super-fast internet connection is fibre broadband which BT markets as ‘BT Infinity’. Want to clear another party? The technical name for this technology is VDSL which stands for Very-high-bit-rate Digital Subscriber Line.
In essence VDSL moves the local exchange to your local BT telephone wiring cabinet (that’s the one with a BT Openreach engineer – head deep in the cabinet, builders crack facing the road).
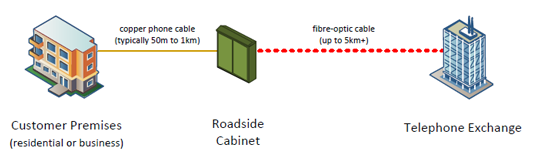
In practical terms a VDSL broadband connection gives you much faster internet speeds, normally between 20 to 70mbps as long as you live within about a mile from the BT wiring cabinet.
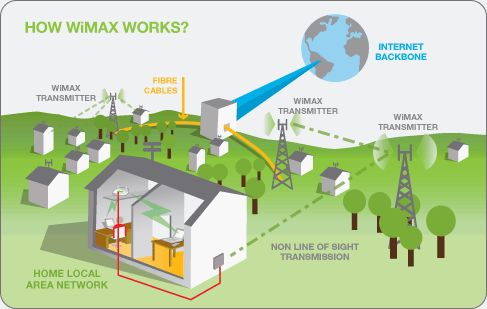
Living in the sticks? If you’re in the countryside normal telephone based broadband is flaky at best. Well you can get your internet connection using a radio connection. Ready for the acronym – well it’s WiMAX (Worldwide Interoperability for Microwave Access).
This technology has been designed to work over long distances just as long as for most of that distance you have a line of sight between your house and the WiMAX transmitter. See diagram below.
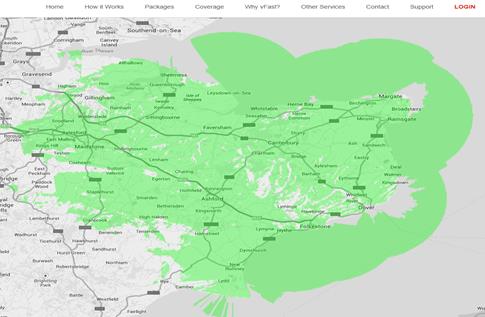
In the Kent area the main provider of WiMAX is a company call VFAST (www.vfast.co.uk). As with most broadband providers, you can go to their website, enter your postcode and see if WiMAX is available in your area. As you can see from the coverage map below, the Kentish fishing community is well catered for.
You want more ways to access the internet? Well you can use a domestic satellite setup, the mobile phone network, direct cable connection or a good old fashion modem. So let me try to distil all these various ways to connect to the internet into a table with pros and cons for each option.
Normal Telephone Broadband (ADSL)
Speed: Poor to Moderate / under 1 to 10 mbps
Cost: Normally free to install & cheap monthly subscription
Guide price: Around £10 per month (without line rental)
Pros: Lots of options and services available and works well if you’re close enough to your local telephone exchange
Cons: Gets slow and unreliable if you’re over 3 miles away from your local telephone exchange
Fibre Broadband (VDSL)
Speed: Moderate to very good / between 15 to 70 mbps
Cost: Free or a small charge to install & fair monthly subscription
Guide price: Around £15 per month (without line rental)
Pros: Fast and reliable internet connection
Cons: Patchy coverage at the moment (it will never reach the remote countryside)
Microwave Broadband (WiMAX)
Speed: Moderate / about 15 to 24mbps
Cost: Expensive to install & fair monthly subscription
Guide price: about £250 to install, around £25 per month
Pros: Allows internet access to remote areas
Cons: Can get affected by weather conditions and moving objects such as trees blowing in the wind
Satellite Broadband
Speed: Moderate to Good / about 20mbps
Cost: Expensive to install & high monthly costs with low data allowance
Guide price: About £400 to £600 to install & £70 per month
Pros: Satellite broadband should work anywhere in the UK
Cons: Can get affected by weather conditions and can have a high latency which adds a delay to video streaming
Mobile Network Broadband
Speed: Poor to moderate / from under 1 to 20mbps
Cost: Normally a small cost for the hardware (USB dongle) & high monthly costs with low data allowance
Guide price: About £50 to install & £20 per month
Pros: Works without wires
Cons: High speed mobile internet access is very patchy outside large urban areas
The survivor’s guide to Wireless Hotspots
As a computer security expert with over 25 years experience in the industry, it often surprises me just how trusting people are when it comes to sending sensitive or personal information using public internet access points such as free wireless hotspots. In the last few years smart phones and laptops have become essential tools for business people with wanderlust and that mid-morning coffee while perusing your e-mail makes you feel like the very epitome of a master of the digital world.
The only problem is while you are sending those bank details to Fred in accounts along with your internet banking sign-on credentials the guy in the corner is taking a copy of your e-mail. What that naughty man is doing is wireless eavesdropping and it is becoming an increasing problem, especially in public areas that offer free wireless hotspots such as a number of coffee outlets and restaurant chains.
Here are my top three tips to avoid becoming part of the increasingly high number of people that have suffered identity theft. But first the science bit. Have you ever wondered what those three letter acronyms WEP and WPA were? Well most people (including IT people) think that WEP stands for ‘Wireless Encryption Protocol’ or some such thing. Well folks, you can be a hit at your next dinner party by knowing that WEP stands for ‘Wired Equivalent Protocol’ and does not encrypt or hide your private e-mails or colourful web surfing in any way. WPA ‘Wi-Fi protected Access’ and WPA2 (the shiny new version of WPA) do try to encrypt your data and offer a certain amount of protection.
1) Turn wireless off and only use 3G/4G – If you are not too badly battered by the storms of the current economic climate and can afford an unlimited 3G/4G data package and can also get a good 3G/4G signal then don’t use free wireless hotspots. I’m not saying that 3G/4G is 100% secure but it’s a great deal more difficult to eavesdrop on a 3G network then a wireless one.
2) Use the padlock – When web surfing, never enter any personal or sensitive information on a web page unless you see the little padlock (or green address bar) on your web browser. The padlock signifies that anything you send or receive is encrypted and should not be accessible by someone eavesdropping.
3) Try to avoid using e-mail – I know, I know, don’t shoot the messenger! Let me explain; standard e-mail uses something called SMTP (simple messaging transfer protocol), another one to impress your dinner party guests. This e-mail system is as old as the hills and is completely insecure. Worst of all, the eavesdropper will be able to read both e-mails you send and e-mails that you receive. Even if you are careful not to send any sensitive e-mails, sensitive e-mails may be sent to you automatically. There are many ways to improve e-mail security on smart phones and laptops but in short if you are unsure if your e-mail client is secure try to minimise the use of e-mails while on a wireless hotspot.
The survivor’s guide to Memory Sticks
Whether you call them thumb drives, flash memory, USB storage or just those thingies, memory sticks are a brilliant way to transport all your important information in your pocket. They’re cheap, capacious and easy to use. Unfortunately most memory sticks are not indestructible or secure.
So first let me summarize what that little piece of plastic snuggling up to your house keys actually is. Well in essence a memory stick is a bunch of memory chips stuck on a circuit board with a USB (Universal Serial Bus) connector at one end. So far so geeky, the problem is that the memory chips are not designed to work forever, they will stop working after a period of use. Manufacturers will tell you that the life span of a memory stick is around 100,000 files copied to and from your device which means for most people your memory stick should still last many years before it pops its clogs. Saying that as you don’t use your laptop as a fun bath time toy, a memory stick will die quicker if you leave it in – and I apologise for the expression – your sweaty trouser pocket for long periods of time.
Tip One: Don’t trust the little blighters to keep your information safe and sound forever. Always keep a second copy of your data on a second memory stick or on your computer hard drive.
The other major problem with memory sticks is one of security. The very fact that sticks are so portable and easy to use makes them a potent weapon in your arsenal of useful technologies. But as anyone who has wielded a sword will tell you beware of that double edge. If you wish to carry around with you recipes for layer cake and amusing videos of kittens stuck in footwear then good luck to you and always remember to pre-heat the oven. If however you use your memory stick to transport customer data, bank account details, medical records etc. then you should consider using an encrypted memory stick. Encrypted memory sticks are the same as normal ones with the addition of a password to gain access to the memory stick’s content. I favour hardware encrypted memory sticks - they are a bit more expensive but offer a greater level of security and also delete the contents of the device if you enter an incorrect password 8 or 10 times in a row (which is not a problem if you heed tip one).
Tip Two: Use an encrypted memory stick to protect private or sensitive information.
My dear chap I hear you say, you’re being coy, tell us which memory sticks we should be buying. Well here are a few devices that I have used successfully, but there are many more in the market that I’m sure will do an equally good job and before you ask I don’t have any affiliations with any of the manufactures.
Basic model: SanDisk Cruzer – a good compact unit which comes with encryption software (price around £10 to £15 for 16 Gb)
Secure model: Kingston DataTraveler Vault (Privacy Edition) – hardware encrypted device with a rugged metal case (price around £30 for 8 Gb)
Premium (Paranoid) model: Ironkey Personal - a military-grade piece of kit for people with very sensitive data to protect and a very large wallet (price around £70 for 4Gb)
The message is simple; love your memory stick but never trust it. Would you want the person next to you on the train who picks up your mislaid stick reading the information in it? If not use encryption.
The survivor’s guide to Passwords
If there’s one thing about the digital world that drives me crazy it’s trying to remember all the user names and passwords you need to do almost anything on the internet these days. Yes I know I’m a digital security specialist but I’m only human so I, like you, use the same password for multiple sites and, just between you and me, I have on occasion written a password down on a sticky note. I’m not going to spend the next few minutes of your reading time extolling the virtues of using long and complicated passwords that include letters, numbers, symbols and quadratic equations in them. In fact I’m not going to tell you anything about how to create a secure password. Wait, bear with me; I do want to tell you just how the naughty people (and virtuous digital forensic folk) do break passwords. So you will have a better understanding as to why you should use long passwords for some systems and simpler and easy to remember passwords for others.
So firstly how do the bad guys get your passwords? Well the easiest way is to physically search for that post-it note under the keyboard or search for that digital post-it note app on your stolen smart phone. So if you need to write your passwords down – hide them away. If you’re an old fashioned ink and quill type of person, store your login details in a place a little bit more subtle than the top draw of your desk. If you’re a hip and trendy dude that knows all about the inter web then store your passwords and the like in a password safe. A password what? A password safe, sometimes called a password vault is a small program /app that you install on your computer or smart phone that encrypts all of your passwords. Guess what - to unlock your password safe you need to enter a password, but hey, you only need to remember one password not all of them - so make it a good one.
A hacker type would acquire passwords over a wired or wireless network as I described in my ‘Hotspot’ article.
Lastly the evil ones will try to discover your password by trying to guess it, a process called password cracking. This is where I want to tell you something that most lay people don’t understand. The strength of a password relies on the complexity of the password and the number of guesses you are allowed to use to discover it. A modern password cracking program can guess millions of passwords a second but you can’t use such a mischievous piece of software to logon to an internet bank for example, because the bank will get grumpy and disable the account after a few bad login attempts. Conversely if you give me a password protected document I can let a password cracker run on it for days and days until it guesses the right password (a service that Invicta Digital offers for the security focused but forgetful client).
So in summary, if you have to write down your passwords keep them safe and use more complicated passwords on systems that never get angry at large amounts of incorrect password attempts. And finally try to use separate passwords for all your important websites. You’ll look pretty foolish if your bank account gets cleaned out because you used the same password as your favourite on-line games account which just got hacked.
The survivor’s guide to Email
Happy birthday – the email system that most of us use today is 35 years old (well at time of writing anyway). POP3 (Post Office Protocol version 3) is still the standard way that people send and receive email through the internet, and like most of the original systems designed for the internet back then it was written without almost any thought for security. Back in those days the internet was mainly used by academic institutions and scientists in the 80s and they were a very trusting bunch with a dubious taste for shoulder pads and Gloria Estefan. So let’s home in on a few of the less well known flaws in email that could cause you to have a very bad day. And not just because your inbox is full up again with adverts for personal bodily enhancement equipment and urgent requests from western African royalty asking for help transferring their considerable wealth out of the country.
One of the most important things you need to know about email is the sender address is purely informational. That is to say it does not have to relate to the actual sender. On my last birthday my beloved scallywag of a wife emailed me birthday greetings from ‘bill.gates@microsoft.com’, ‘god@sky.com’ and slightly in bad taste ‘george.harrison@heaven.com’. The one saving grace is that if you try to reply to that ethereal Beatle your email will be sent skywards and will in all probability be returned as undeliverable – sorry George.
So the bad guys can send you emails that look like they are from a legitimate sender but they cannot use a fake sender to start an email conversation. So the evil wizards of spam land use something called a Phishing email. Why fishing spelt with a ‘ph’? Well hackers of old used to spell words incorrectly so as to fool law enforcement search tools that were looking for particular phrases that pointed to hacking activities – either that or they couldn’t spell.
In essence a Phishing email is a message sent from, what would appear to be, a genuine source, a bank, the Inland Revenue, on-line shop etc. That email will normally say something along the lines of your account has been suspended or there is a problem with the payment for your internet purchase or some such thing. The email will have a hyperlink or button that you must press to go to the sender’s web site so you can fix the problem. If you click on the link you will be sent to a web site, set up by the bad guys to mimic the real one. After which if you logon to this phoney site your details will be captured and used for nefarious purposes.
If, or more probably, when, you receive an email simply hover your mouse cursor over the link in the message. After a second the web address of the site the email will send you to will appear. Now look at the address and check that it is the same as the email address (the bit after the ’@’ symbol). If the addresses match and the internet address looks legitimate then you should be safe. E.g. you receive an email from ‘customer.support@amazon.co.uk’. If the link in the email goes to ‘amazon.co.uk’ you’re good to go, if the link goes to ‘badguys.ch’ then it’s a phishing email - delete it.
Phishing emails can look very genuine, the simple advice is be careful when clicking on links in email or indeed opening email attachments. Attachments not only can have bogus links but can install malware on your system as well. I had a client a few years ago that received an email from her bank, clicked on the link, signed on to what looked like her bank’s internet logon page and the next day found her account had been cleared out – over £100,000! With a little care emails have been and still are the single biggest boost to business productivity, now if you’ll excuse me I’ve just received a birthday greetings email from ‘thequeen@buckhouse.com’ - Hmmmm.












